Crude benchmarks of NaCl and scrypt in the browser
Sun 31 Mar 2013 14:50 EDT
As I just wrote, I’ve ported libraries for cryptography (js-nacl) and password-based key derivation (js-scrypt) to Javascript.
Some browsers are faster at running these cryptographic routines than others. The results below are from casual (nay, unscientific!) speed measurements in the browsers I had handy on my machine.
The setup:
- Chrome 26.0.1410.43
- Safari 5.1.8 (6534.58.2)
- Aurora 21.0a2 (2013-03-30)
- Firefox 19.0.2
- Macbook Air late 2010 (3,1), 1.6 GHz Core 2 Duo, 4 GB RAM, OS X 10.6.8
I had to exclude Firefox from the nacl tests, since it lacks
window.crypto.getRandomValues.
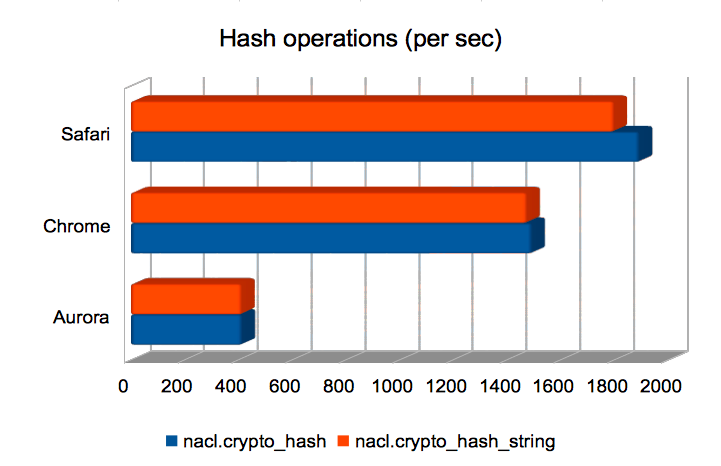
Hashing strings/bytes with SHA-512
Here we see Safari has the edge. Aurora is oddly slow.
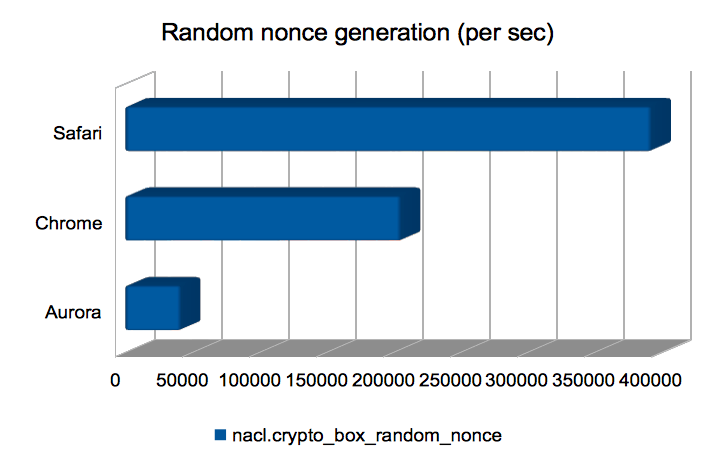
Computing random nonces
This is a thin wrapper over window.crypto.getRandomValues. Safari
wins hands-down here. I wonder how good the generated randomness is?
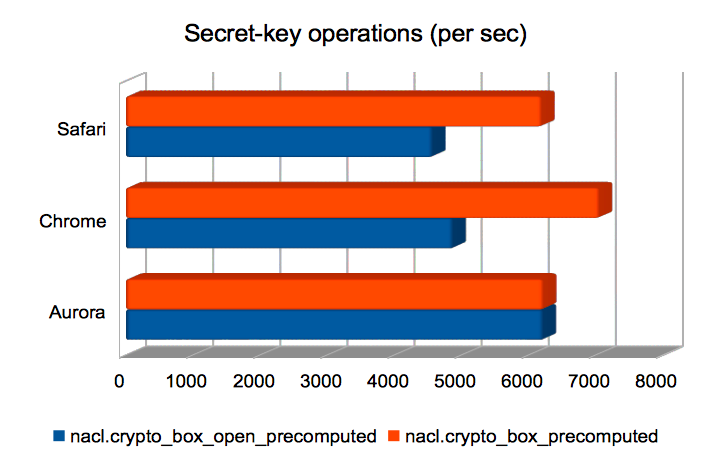
Authenticated encryption using a shared key
These are Salsa20/Poly1305 authenticated encryptions using a precomputed shared key. Broadly speaking, boxing was quicker than unboxing. The browsers perform roughly equally here.
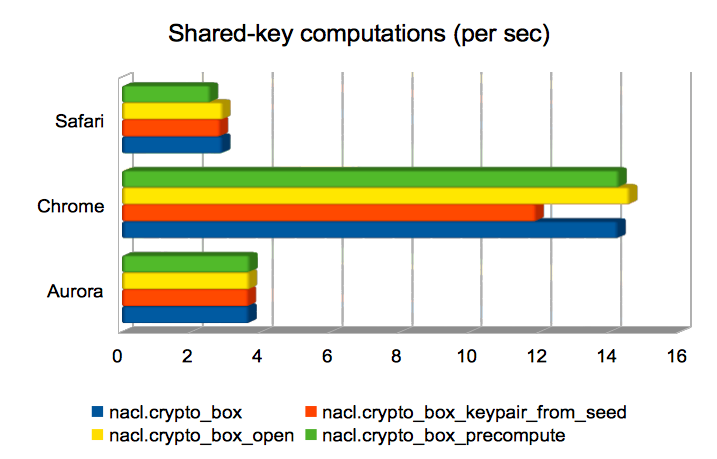
Computing a shared key from public/private keys
These are operations whose runtime is dominated by the computation of
a Curve25519 operation. In three of the
four cases, the operation is used to compute a Diffie-Hellman shared
key from a public key and a secret key; in the remaining case
(crypto_box_keypair_from_seed) it is used to compute a public key
from a secret key. Chrome is significantly faster than the other
browsers here.
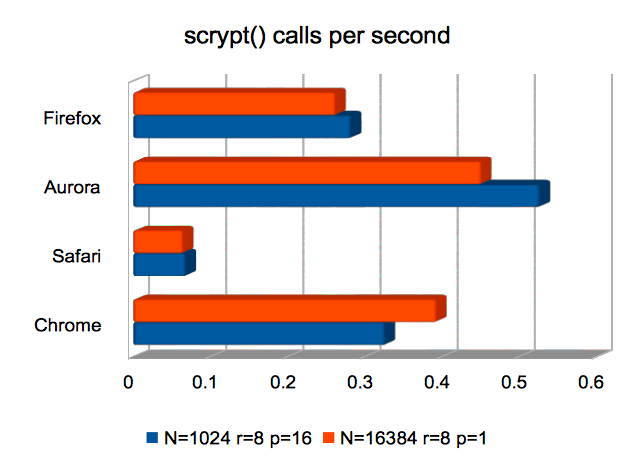
scrypt Key Derivation Function
Here, Safari is the only browser that underperforms significantly. The
other three all compute an scrypt-derived key in 2–4 seconds,
using defaults suggested by the scrypt paper as being suitable for
interactive login.
Conclusions
scrypt is slow. Precompute Diffie-Hellman shared keys where you can.
